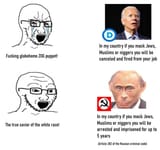
>>512144852 (OP)He's not technically wrong.
Authentication is a pillar of cybersecurity.
If not its fundation.
It's simply not possible to setup a secured communication tunnel over a untrusted medium (which internet is) without it.
Without authentication, any clown owning a node of the network can simply intercept your RSA handshake and replace your correspondent public key with its own compromised public key.
Yes. The whole PKI certyificate infrastructure is supposed to tackle that issue. But in practice, it does not.
Those trusted root certificate? They cannot be trusted at all.
The only thing that work is physically transporting keys in person. And to renew them frequently.
That's what modern armies still do.