Anonymous
ID: twnhwT1a
6/29/2025, 8:00:10 AM No.6267240
Zailgo e0 Game - Investigation Summary (Part 1/3)
Game Overview
Game Name: "Zailgo e0" (also referred to as "Zalgo")
Creator: @Wedtm on X (Twitter)
Type: Cybersecurity/hacking challenge involving port knocking and SSH access
Goal: Gain SSH access to Docker containers running in a Kubernetes cluster
Core Challenge Description (from @Wedtm)
"The scanners are Docker containers that are running in a Kubernetes cluster here at my house that I have a bunch of IPv6 addresses pointed at. In order to access them, you need to port knock. If you're not familiar with port knocking, it's basically sending a request to a port that is closed. The destination server, just because the port is not accepting a connection, can still see that you have made an attempt to connect to that port. So you have to do that with three different ports in the right order, and then SSH will open up. Once SSH opens up, you also have to have an SSH key that's valid, which you can generate those and get keys from those in certain places."
Key Clues Discovered
1. Initial Scanner Interface
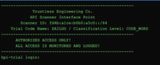
Trustless Engineering Co.
HPI Scanner Interface Point
Scanner ID: fd4b:a1ce:b0b0:a5c0::/64
Trial Code Name: ZAILGO / Classification Level: CODE_WORD
hpi-trial login:
2. Critical Port Information
Port 25519: Confirmed as one of the three knock ports (position "2" in sequence)
Sequence Pattern: "2 3 1" - this is the ORDER, not the port numbers
Total Process: 3 port knocks + SSH opens (4 total steps)
3. IPv6 Address Translation
Original (private): fd4b:a1ce:b0b0:a5c0::/64
Public equivalent: 2607:b4c0:a1ce:b0b0:a5c0::/64 (Trustless Engineering's address space)
Key insight: The fd4b: prefix was converted to 2607:b4c0: for the public network
4. Cryptographic References
Alice and Bob pattern:
a1ce = "Alice"
b0b0 = "Bob"
Ed25519 reference: Port 25519 relates to the Ed25519 cryptographic curve
Penrose Tiles book: "Penrose Tiles to Trapdoor Ciphers...and the Return of Dr. Matrix" by Martin Gardner (learning material)
5. Numerical Clues from Game
Original numbers: 2504, 0425, 254, 425, 1995, 32768, 520, 2607, 3000, 103, 666, 15300, 135, 768, 3791, 112, 25519
Additional numbers discovered: 420, 3791, 112
Date reference: "25th of the 4th" (possibly relating to ports 2504, 0425, 254, 425)
6. Special URL Clue
URL in Miles' bio: https://2130706433
Decoded: 2130706433 = 127.0.0.1 (localhost in decimal format)
Significance: Suggests converting decimals to IP components for IPv6 address construction
Game Overview
Game Name: "Zailgo e0" (also referred to as "Zalgo")
Creator: @Wedtm on X (Twitter)
Type: Cybersecurity/hacking challenge involving port knocking and SSH access
Goal: Gain SSH access to Docker containers running in a Kubernetes cluster
Core Challenge Description (from @Wedtm)
"The scanners are Docker containers that are running in a Kubernetes cluster here at my house that I have a bunch of IPv6 addresses pointed at. In order to access them, you need to port knock. If you're not familiar with port knocking, it's basically sending a request to a port that is closed. The destination server, just because the port is not accepting a connection, can still see that you have made an attempt to connect to that port. So you have to do that with three different ports in the right order, and then SSH will open up. Once SSH opens up, you also have to have an SSH key that's valid, which you can generate those and get keys from those in certain places."
Key Clues Discovered
1. Initial Scanner Interface
Trustless Engineering Co.
HPI Scanner Interface Point
Scanner ID: fd4b:a1ce:b0b0:a5c0::/64
Trial Code Name: ZAILGO / Classification Level: CODE_WORD
hpi-trial login:
2. Critical Port Information
Port 25519: Confirmed as one of the three knock ports (position "2" in sequence)
Sequence Pattern: "2 3 1" - this is the ORDER, not the port numbers
Total Process: 3 port knocks + SSH opens (4 total steps)
3. IPv6 Address Translation
Original (private): fd4b:a1ce:b0b0:a5c0::/64
Public equivalent: 2607:b4c0:a1ce:b0b0:a5c0::/64 (Trustless Engineering's address space)
Key insight: The fd4b: prefix was converted to 2607:b4c0: for the public network
4. Cryptographic References
Alice and Bob pattern:
a1ce = "Alice"
b0b0 = "Bob"
Ed25519 reference: Port 25519 relates to the Ed25519 cryptographic curve
Penrose Tiles book: "Penrose Tiles to Trapdoor Ciphers...and the Return of Dr. Matrix" by Martin Gardner (learning material)
5. Numerical Clues from Game
Original numbers: 2504, 0425, 254, 425, 1995, 32768, 520, 2607, 3000, 103, 666, 15300, 135, 768, 3791, 112, 25519
Additional numbers discovered: 420, 3791, 112
Date reference: "25th of the 4th" (possibly relating to ports 2504, 0425, 254, 425)
6. Special URL Clue
URL in Miles' bio: https://2130706433
Decoded: 2130706433 = 127.0.0.1 (localhost in decimal format)
Significance: Suggests converting decimals to IP components for IPv6 address construction