Anonymous
(ID: GB7tlMlb)
 8/2/2025, 8:54:44 PM
No.512056519
>>512056844
>>512056997
>>512057154
>>512057366
>>512058040
>>512058360
>>512058366
>>512060034
>>512060184
>>512060766
>>512061342
>>512061632
>>512061751
>>512062010
>>512062111
>>512062429
>>512063030
>>512064952
>>512065689
>>512065768
>>512067215
>>512067601
>>512068296
>>512070192
>>512071673
>>512071700
>>512074430
>>512075876
>>512076360
>>512078143
>>512079035
>>512081139
>>512083340
>>512083361
>>512087759
>>512088565
>>512088751
>>512089818
>>512090058
>>512090113
>>512091413
>>512091592
>>512092141
>>512092668
8/2/2025, 8:54:44 PM
No.512056519
>>512056844
>>512056997
>>512057154
>>512057366
>>512058040
>>512058360
>>512058366
>>512060034
>>512060184
>>512060766
>>512061342
>>512061632
>>512061751
>>512062010
>>512062111
>>512062429
>>512063030
>>512064952
>>512065689
>>512065768
>>512067215
>>512067601
>>512068296
>>512070192
>>512071673
>>512071700
>>512074430
>>512075876
>>512076360
>>512078143
>>512079035
>>512081139
>>512083340
>>512083361
>>512087759
>>512088565
>>512088751
>>512089818
>>512090058
>>512090113
>>512091413
>>512091592
>>512092141
>>512092668
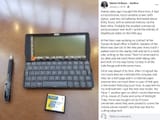
Glowniggers HATE pocket PCs
image.jpg
md5: b3745595... 🔍
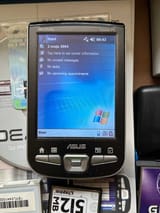
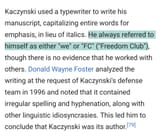
They are like smartphones with no phone or internet connection. They also store their files in a RAM disk so as long as you dont install the backup coin battery you can just yeet the main battery and erase everything. They also use proprietary connectors so the cops diagnostic tools wont work anyway.