Search Results
7/9/2025, 3:17:47 PM
>>105802125
New attack that affects TLS:
https://opossum-attack.com/
>Application Layer Desynchronization using Opportunistic TLS
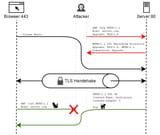
>The Opossum attack exploits issues in the authentication mechanism of TLS (identified in the ALPACA attack) to desynchronize a client and a server, even if all current ALPACA countermeasures are in place. To do this, Opossum attacks small differences on the application layer between implicit TLS (where TLS is established immediately) and opportunistic TLS (where connections start in plaintext and upgrade to TLS). If a server supports both methods for a given protocol, when a client attempts to connect using one method, an attacker can redirect the connection to use the other method, creating a mismatch in protocol expectations between client and server.
>In the attack, a man-in-the-middle attacker intercepts a client's TLS connection intended for an implicit TLS connection (e.g., HTTPS on port 443). The attacker establishes their own plaintext connection to the server's opportunistic TLS port (e.g., HTTP on port 80), sends a malicious request with TLS upgrade headers, then forwards the client's connection to the server as if it were part of its own connection on port 80. After the TLS handshake completes, both parties send messages simultaneously - creating a desynchronization where the client receives the wrong response to their request. The attacker can now delay the response from the server to the client, such that it appears to the client as if the server sent the application data message in response to its request. In the example in Figure 1, the attack causes the client to receive the answer "dog", even though it requested the resource "cat". This desynchronization persists for all subsequent requests in the connection.
New attack that affects TLS:
https://opossum-attack.com/
>Application Layer Desynchronization using Opportunistic TLS
>The Opossum attack exploits issues in the authentication mechanism of TLS (identified in the ALPACA attack) to desynchronize a client and a server, even if all current ALPACA countermeasures are in place. To do this, Opossum attacks small differences on the application layer between implicit TLS (where TLS is established immediately) and opportunistic TLS (where connections start in plaintext and upgrade to TLS). If a server supports both methods for a given protocol, when a client attempts to connect using one method, an attacker can redirect the connection to use the other method, creating a mismatch in protocol expectations between client and server.
>In the attack, a man-in-the-middle attacker intercepts a client's TLS connection intended for an implicit TLS connection (e.g., HTTPS on port 443). The attacker establishes their own plaintext connection to the server's opportunistic TLS port (e.g., HTTP on port 80), sends a malicious request with TLS upgrade headers, then forwards the client's connection to the server as if it were part of its own connection on port 80. After the TLS handshake completes, both parties send messages simultaneously - creating a desynchronization where the client receives the wrong response to their request. The attacker can now delay the response from the server to the client, such that it appears to the client as if the server sent the application data message in response to its request. In the example in Figure 1, the attack causes the client to receive the answer "dog", even though it requested the resource "cat". This desynchronization persists for all subsequent requests in the connection.
Page 1