Anonymous
8/26/2025, 10:58:08 AM
No.106387910
>>106387925
>>106387934
>>106387954
>>106388460
>>106388556
>>106388564
>>106390573
>>106391289
>>106391747
>>106393108
>>106393510
>>106393943
>>106394843
>>106395626
I'm gonna write password into paper notebooks
Capture.png
md5: e1a6edcb... 🔍
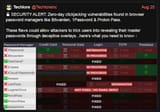
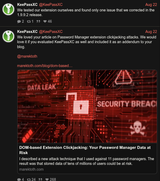
Why was password manager so insecure piece of shit, Look. they found an clickjacking vulnerabilities in browser password managers
Time to write passwords in the paper notebook and keep it private. So nobody could see it!
Time to write passwords in the paper notebook and keep it private. So nobody could see it!