>>106546998
Yeah there is.
Compiling playground v0.0.1 (/playground)
Finished `dev` profile [unoptimized + debuginfo] target(s) in 0.55s
Running `/playground/.rustup/toolchains/nightly-x86_64-unknown-linux-gnu/bin/cargo-miri runner target/miri/x86_64-unknown-linux-gnu/debug/playground`
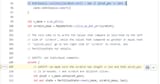
error: Undefined Behavior: trying to retag from <296> for Unique permission at alloc157[0x0], but that tag only grants SharedReadOnly permission for this location
--> src/main.rs:12:27
|
12 | let target = unsafe { std::mem::transmute::<&u64, &mut [u64; 3]>(&arr[0]) };
| ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^ this error occurs as part of retag at alloc157[0x0..0x18]
|
= help: this indicates a potential bug in the program: it performed an invalid operation, but the Stacked Borrows rules it violated are still experimental
= help: see
https://github.com/rust-lang/unsafe-code-guidelines/blob/master/wip/stacked-borrows.md for further information
help: <296> was created by a SharedReadOnly retag at offsets [0x0..0x8]
--> src/main.rs:12:70
|
12 | let target = unsafe { std::mem::transmute::<&u64, &mut [u64; 3]>(&arr[0]) };
| ^^^^^^^
= note: BACKTRACE (of the first span):
= note: inside `main` at src/main.rs:12:27: 12:78
note: some details are omitted, run with `MIRIFLAGS=-Zmiri-backtrace=full` for a verbose backtrace
error: aborting due to 1 previous error